This time, I'll try to explain how to exploit a software that have a SEH protection on its system called BigAnt Server. SEH is an exception handler to protect the EIP to be overflowed by the abnormal flow on the software. This will force us to use different attack vector and technique because if we use the same technique as in the Direct Return Exploit the attack won't work because of SEH.
BigAnt server is an Internet Messenger server. The version of the software that used in this post is 2.52 Service Pack 5.
Lets get started.. >:D
- First thing to do of couse installing the software on the xp machine.
- The server runs its service on port 6660. We will attack that port.
- To make a proper script for the attack we must have a BigAnt client because we can see the communication between them. What packet was sent by the client to the server and vice versa.
- In this post we will try to fuzz the USV command on the server.
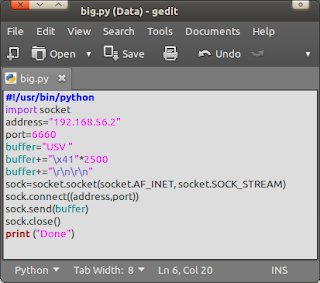
- Make a fuzzer with this script.
Spoiler:
- The script will send 2500 'A' character on the server.
- In this state if you execute the script nothing will happen in the BigAnt because of the SEH protection.
- SEH working in the background, to see that we must use debugger. Again, I'll use OllyDbg.
- Open your debugger and attach to AntServer process. Pay attention to what you attach because BigAnt create 3 services on the sytem AvServer, AntServer, and AntAdmin.
- Ok, now execute the fuzzer and see what happen in OllyDbg.
- As you can see above, the EIP isn't overwritten by the fuzzer directly because of the SEH. To view what happen in SEH, click View>SEH chain.
- The SEH handle the excess 'A' character. To transmit the char into the EIP press Shift+F9
- In the bottom right of the OllyDbg windows, we can see that the fuzzer's data sent to the application also entered the stack memory. To see it right click on the stack line then click follow in dump.
- To pass the SEH protection we must find the POP POP RETN command on one of the modules that loaded by BigAnt. The module must not have SafeSEH ON, and DLLCHARACTERISTICS_NO_SEH in it. Usually, modules that don't have it is a third party module outside Windows. But, in this case BigAnt don't have a modules in its system, so we must use the modules from Windows.
- We will use VBAJET32.dll located in C:\\Windows\system32 as the door to pass the SEH as the modules is also loaded by BigAnt.
- After that, we must find the POP POP RETN command on this module. Open your module then right click > Search for > Sequence of Commands.
- Enter POP r32, POP r32, and RETN on the search box.
- Here's what we will get. The address of POP POP and RETN on the VBAJET32.dll module.
- Ok, next step we must find the address where the SEH is overwritten. As usual, we will use pattern_create and pattern_offset to do this.
- Make a pattern 2500 bytes long then insert it on the fuzzer.
Spoiler:
- Execute it, then see what happen in OllyDbg. Don't forget to restart both OllyDbg and BigAnt server first.
- Use pattern_offset to get the exact address.
# ./pattern_offset.rb 42326742
966
- Ok, next lets try to overwrite the SEH with our own word like DEADBEEF. To do it, change the fuzzer script a little.
Spoiler:
- Why the data sent is not 966 bytes but 962 bytes? because 4 bytes before SEH address will be overwritten by the 'cc' character.
- Execute it and see what will happen in SEH Chain.
- Looks good, next thing lets try to overwrite the SEH with the address of POP POP RETN on the VBAJET32.dll module. Change the script again.
Spoiler:
- Before execute it. Place a breakpoint on the POP POP RETN address on VBAJET32.dll module.
- Now, execute it then see what SEH Chain will display.
- Press Shift+F9 to continue the process to VBAJET32.dll then press it again to continue the POP POP RETN sequence located in the module. After that press F7 until the process reach the RETN command.
- The problem now is that we only have 4 bytes to store our payload. That definitely doesn't enough to store our payload. So we must find another process that big enough to store our payload.
- Right click on the first CC (012CFD7C)>Follow in Dump >Selection. By doing this OllyDbg will show us the address where we can store our payload.
- So, how we use that? With a little calculation we can know the size available for us to be used as the place to store the payload. The starting address is 016FFD84 and the end address is 016FFFFC. Convert that into decimal then decrease the last address with the starting address and we will get the exact size to place our payload.
- To order the CPU to the new big location, we can use JMP SHORT command. JMP SHORT used to order the CPU to jump several bytes forward then start the execution process from that location.
- I'll explain about JMP SHORT and how to use it in the other post.
- Next, generate the payload using msfweb.
- Why there are 0x20 and 0x25 in the Restricted Characters columns? It is a bad character. More details here.
- Generated payload.
- Insert it to our fuzzer.
Spoiler:
- Execute the fuzzer then connect using telnet to the target.
Success.. ^_^b
"the quieter you become, the more you are able to hear.."































0 comments:
Post a Comment