Again, in this post I will try to exploit a software using the Buffer Overflow technique. The software is called VUPlayer.
Lets do some testing first to make the software crashed. That will be my attack vector.
Alhamdulillah, this morning I'm succeeded to make the software crashed in the first try. Here's what I did.
- Of course installing VUPlayer in my Windows XP machine.
- Okay, I want to try adding url. (of course the url is not the valid one.. :P )
- Making 1000 'A' character in notepad.
- Clicking "Add URL" menu on the player then insert the character.
- Click OK.
- Hmm.. the player seems still running. Lets increase the character 10 times into 10000 'A' character >:)
- Again, insert it in the 'Add URL' section on the software.
- Click OK, and then....
- Booom, the software crashed.. :D
- Now lets see with OllyDbg when the software crashed whether the EIP is overflowed or not.
- Great, looks like this bug can be our door to exploit the system.
- Next step, I'll try to search the address where the EIP is overwritten. Lets go to metasploit directory to make a pattern.
- Lets open it in the xp.
- Copy, then paste at the "Add URL" menu in the software.
- Here's what we will get.
- Back to the metasploit pattern tools. Now, we must use pattern_offset script to find the exact address.
- Next step, lets try to overwrite the EIP with our word like "DEADBEEF" (again.)
- To help me do this, I make a fuzzer with a python language like this.
- It will generate a file named "agoes.txt" that contain the junk character plus our DEADBEEF character.
- Lets execute it.
- Open it in the xp.
- Copy and then paste in the vuplayer.
- Here's what we got.
- Success..
- Okay, next I'll try to fill the ESP with NOP.
- Edit the fuzzer script become like this.
- Generate the file and then open in XP.
- Copy, then paste in the vuplayer.
- Click Ok, and here's what we got.
- Looking good, next step. Searching the address of JMP ESP in the SHELL32.dll module.
- Here it is.
- Lets insert it to our fuzzer. Dont' forget to change it into little endian format.
7C9D30D7 = \xD7\x30\x9D\x7C
- Before executing the script. Lets generate the payload too.
- Generating "Windows Bind Shell" payload using msfweb.
- Final modification on the fuzzer script.
- Generate the file then open in XP.
- Copy all code, then paste in vuplayer.
- Hmm... still have to do some trial and error because it don't work.
- But there's this error everytime I open vuplayer with OllyDbg. Maybe this is the key. Have to research it.. :)
- After doing some research, I think maybe I should try use the JMP ESP address that located in the BASS module because this module seems suspicious and vulnerable.
- Change the fuzzer script a little.
- Generate the new file then open in XP.
- Wow, the character seems very strange. :D
- Doesn't matter, copy it then paste in VUPlayer.
- Connect to the payload in port 4444 using telnet.
Finnally, Its working..
Exploitation successful.
(^_^)v
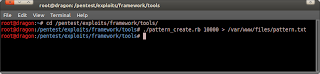
# cd /pentest/exploits/framework/tools- Because the software crashed when I make 10000 'A' character. I'll generate 10000 bytes character too this time.
# ./pattern_create 10000 > /var/www/files/pattern.txt
- Lets open it in the xp.
- Copy, then paste at the "Add URL" menu in the software.
- Here's what we will get.
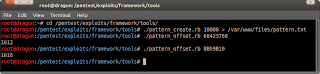
- Back to the metasploit pattern tools. Now, we must use pattern_offset script to find the exact address.
# ./pattern_offset 68423768
1012
# ./pattern_offset 8Bh9Bi0
1016
- Next step, lets try to overwrite the EIP with our word like "DEADBEEF" (again.)
- To help me do this, I make a fuzzer with a python language like this.
Fuzzer:
- Lets execute it.
- Open it in the xp.
- Copy and then paste in the vuplayer.
- Here's what we got.
- Success..
- Okay, next I'll try to fill the ESP with NOP.
- Edit the fuzzer script become like this.
Fuzzer:
# python ./fuzz.py
- Copy, then paste in the vuplayer.
- Click Ok, and here's what we got.
- Looking good, next step. Searching the address of JMP ESP in the SHELL32.dll module.
- Here it is.
- Lets insert it to our fuzzer. Dont' forget to change it into little endian format.
7C9D30D7 = \xD7\x30\x9D\x7C
Fuzzer:
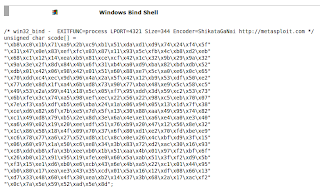
- Generating "Windows Bind Shell" payload using msfweb.
# cd /pentest/exploits/framework2/
# ./msfweb
- Final modification on the fuzzer script.
Fuzzer:
- Copy all code, then paste in vuplayer.
- Hmm... still have to do some trial and error because it don't work.
- But there's this error everytime I open vuplayer with OllyDbg. Maybe this is the key. Have to research it.. :)
- After doing some research, I think maybe I should try use the JMP ESP address that located in the BASS module because this module seems suspicious and vulnerable.
- Change the fuzzer script a little.
Spoiler:
- Wow, the character seems very strange. :D
- Doesn't matter, copy it then paste in VUPlayer.
- Connect to the payload in port 4444 using telnet.
# telnet 192.168.56.101 4444
Finnally, Its working..
Exploitation successful.
(^_^)v
"the quieter you become, the more you are able to hear.."









































4 comments:
After I do with uncounting trial I have found a match payload!!! and After that I look your blog... awsome you find another way to exploit!!!
Ganbatte yo!
great..
glad to hear that.. :D
anyway, thanks for coming by... :)
great :)
thanks..
still have lot thing to study though.. :D
Post a Comment