Hello again,
Lets talk a little about Linux password management.
At first all username and password in Linux is stored in the file /etc/passwd. It is encrypted. But as time goes on and the information security gets serious, this method is changed.
There is a new file at /etc/shadow that used to encrypt the /etc/passwd. So, the file can only be accessed by the root.
Today, my sensei ordered me to do privilege escalation on 192.168.0.21
Here is what I did.
1. First, lets do some information gathering. By using Nmap I also did Service enumeration at once.
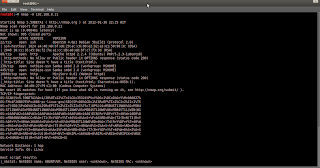
# nmap -A 192.168.0.21
here's the result
2. Notice that at port 10000 there's a webmin service running. Lets check it in browser.
Jackpot, there is the webmin login page.
3. Okay, next step doing vulnerability scanning using Nessus. (tutorial using nessus go here)
Found out that SSH on port 22 is a high vulnurable point.
Trying to exploit it using some tools but what I got is only "zero result".
4. Oh, why not attack the webmin? Lets search the webmin exploit using exploit-db search.
# cd /pentest/exploits/exploitdb/pentest/exploits/exploitdb# ./searchsploit webminand here's the result
5. Note that there's two important things there about the webmin exploit. 'Bruteforce' and 'Arbitrary'. Bruteforce is a method to gain access in the system by trying to enter the password probabilition one by one forcefully. And arbitrary is a method to read the content of a file that supposed prohibited to be read. Lets use the arbitrary. It is an exploit written in Perl (2017.pl a perl code)
# perl platforms/multiple/remote 2017.pl 192.168.0.21 10000 /etc/shadow 0
6. Binggo, from what we get, we know that in the system there are 5 user account. (root,vmware,obama,osama,yomama).
Good to go, next step is cracking these password encryption with John the Ripper. So I'm copied all the content of the file.
Continued to Part 2.







0 comments:
Post a Comment