Nowadays, most people especially engineers have a website. They usually use it to share their activity, show their works, make a portofolio, etc. But, little people concern about the security of their website. They usually won't do something about the security of their website before it is attacked by hacker. They don't know the importance of their web security before someone breaks into it.
In this post, I'll try to show how to gain a root access through a web application. There are a lot of method to do that, this is one of them. The web application that will be used is DVWA(Damn Vulnerable Web Application). You can download it here. The installation is there too.
- Start up your apache and mysql.
- Open dvwa in browser.
- Login with username : admin and password : password.
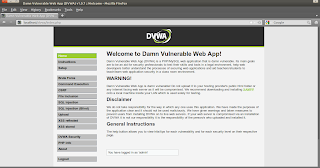
- DVWA main page.
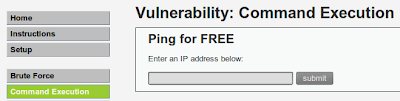
- The vulnerability that I'll use to gain root access from this web is through its "command execution" vulnerability because in a web, this is the most dangerous feature to have. Hacker can get a shell without having to place a backdoor inside the server.
- Set the security level to medium. (because 'low' would be too easy and 'hard' would be too difficult.. :P )
- Lets try to do a normal command.
- Next, lets execute multiple command.
- Lets try to use pipe "|".
- Looking good. Now, lets begin the attack. >:)
- I'll use a local exploit on the system to gain the root access. Before searching the exploit, lets see what version of kernel the system running.
- Search the exploitdb for the local exploit. Using keyword "2.6.39" I found this exploit created by zx2c4 coded in C language.
- After download the exploit, lets compile it first before transferring it to the target. Original Exploit code here.
- Exploit ready to be used.
- Now lets try to upload it using "File Upload" on dvwa. Before doing that, I'll increase dvwa security into High level because it is a rule in my training center.
- Ok, lets try to upload the exploit.
- Whoops, it looks like the server only accept image file to be uploaded.
- Lets try to add image extention into the exploit. I'll make it into exploit.jpeg
- Upload it.
- Good. Now, lets connect to the server using netcat to execute that exploit.
- Back to "Command Execution" feature. (Don't forget to change the dvwa security to medium again)
- Lets see if the exploit is correctly uploaded.
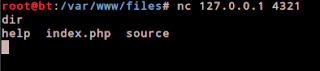
- Now, execute netcat on the dvwa on listening mode.
- Look on the bottom/status bar. The browser will wait for a connection. In backtrack's terminal type this. "nc 127.0.0.1 4321"
- Then, move to the directory where the exploit is located.
- Execute it.
- Not good, the exploit didn't work properly. =,=
- Turns out that I haven't change the permission to execute the exploit. :P
- To change it simply type "chmod 777 exploit.jpeg"
- Next, lets try to execute it again.
-Its running. But the process to spawn a root shell is taking so long. I wonder if the exploit is succeeded. Have to research more.. :)
"the quieter you become, the more you are able to hear.."
- Exploit ready to be used.
- Now lets try to upload it using "File Upload" on dvwa. Before doing that, I'll increase dvwa security into High level because it is a rule in my training center.
- Ok, lets try to upload the exploit.
- Whoops, it looks like the server only accept image file to be uploaded.
- Lets try to add image extention into the exploit. I'll make it into exploit.jpeg
- Upload it.
- Good. Now, lets connect to the server using netcat to execute that exploit.
- Back to "Command Execution" feature. (Don't forget to change the dvwa security to medium again)
- Lets see if the exploit is correctly uploaded.
- Now, execute netcat on the dvwa on listening mode.
- Look on the bottom/status bar. The browser will wait for a connection. In backtrack's terminal type this. "nc 127.0.0.1 4321"
- Then, move to the directory where the exploit is located.
- Execute it.
- Not good, the exploit didn't work properly. =,=
- Turns out that I haven't change the permission to execute the exploit. :P
- To change it simply type "chmod 777 exploit.jpeg"
- Next, lets try to execute it again.
-Its running. But the process to spawn a root shell is taking so long. I wonder if the exploit is succeeded. Have to research more.. :)
"the quieter you become, the more you are able to hear.."
























2 comments:
that was cool, but did u have to tried and succeeded right now with those exploits ?
what's abt that fucking rule of changing security level in the middle of exploitation u can simply upload shell in middle level security.....
Post a Comment